My previous blog post outlined a proposed Diamond Model of Disinformation for analytical pivoting between four features using observables: Victims, Mediums, Messages and Attackers.
A blog post that outlines a theory without attempting to apply it in an operational context and demonstrate its analytical utility would serve little purpose. Let’s consider the 2017 Macron leaks as a two-fold example of a cyber intrusion and a subsequent disinformation campaign. Jean-Baptiste Jeangène-Vilmer’s report for the Atlantic Council (linked above) provides a useful basis of observables for our analysis. This post will be tagged with both ATT&CK and AM!TT techniques.
The first step of this post will be to apply the Diamond Model of Intrusion to the En Marche hack in order to demonstrate the utility of the original framework for cyber intrusions. This will be followed by the application of the proposed Diamond Model of Disinformation to the subsequent disinformation campaign.
Context
On the evening of 5 May, 2017, the #MacronLeaks hashtag began trending on Twitter, with many accounts tweeting about an alleged leak of En Marche’s emails. En Marche was the political campaign supporting Emmanuel Macron, then candidate for the 2017 presidential elections. The leak emerged on social media 48 hours before the second round of the elections on May 7th , which pitted the centrist candidate against Marine Le Pen representing the far-right. It was quickly pointed out by many French media outlets that the leaks were a blatant attempt to manipulate French voters days before the decisive vote following months of disinformation campaigns targeting the elections. Following the leak, En Marche disclosed that it had been compromised and that emails from 5 staff members had been dumped by attackers, with the emails eventually being released and amplified on social media. The leaked emails were dated between March 2009 and 24 April 2017, with the En Marche team having publicly warned that they had been targeted by phishing campaigns as early as December 2016.
Ultimately, the campaign failed to alter the result of the elections, with Macron winning the presidency on 7 May. However, the specific techniques, tactics and procedures (TTPs) employed during this “hack and leak” operation reveal that the perpetrators have established a playbook that is both reflective of past operations and indicative of potential future operations.
The hack
In chronological order, attackers first identified that En Marche used Microsoft OneDrive as a online storage solution, and registered the following domains typosquatting En Marche’s domains (T1583.001):
- onedrive-en-marche.fr
- mail-en-marche.fr
- portal-office.fr
- accounts-of-fice.fr
Three of these domains were registered using Ukrainian phone numbers, and one with a French phone number.
Having identified a list of En Marche staff and their emails, attackers then emailed their targets using an email address spoofing En Marche’s campaign digital manager, Mounir Mahjoubi (T1589.003, T1589.002). The email address was designed to be nearly identical to Mahjoubi’s real address by omitting a single letter- Vilmer provides mounir.mahjobi@… as a potential example (T1585.002).
The email was titled “Recommendations against cyberattacks” and contained instructions for En Marche members to download a document hosted on the malicious domains registered by attackers which contained guidelines on cybersecurity practices. The victims were then prompted to enter their credentials into the realistic-looking OneDrive login portals hosted on the domains (T1566.002). It is unclear whether the attackers used a malicious payload embedded in the purported document to establish a foothold on En Marche’s networks or the legitimate credentials obtained from the malicious domains to login directly into the victims’ email accounts and exfiltrate emails (T1566.001, T1078, T1567).
We have hence enumerated the following ATT&CK TTPs:
- Acquire Infrastructure: Domains T1583.001
- Establish Accounts: Email accounts T1585.002
- Phishing: Spearphishing Link T1566.002
- Phishing: Spearphishing Attachment T1566.001
- Valid Accounts T1078
- Exfiltration from Web Service T1567
We have also enumerated the following atomic observables (IOCs):
- onedrive-en-marche.fr
- mail-en-marche.fr
- portal-office.fr
- accounts-of-fice.fr
Finally, we are able to populate these observables in our diamond model:
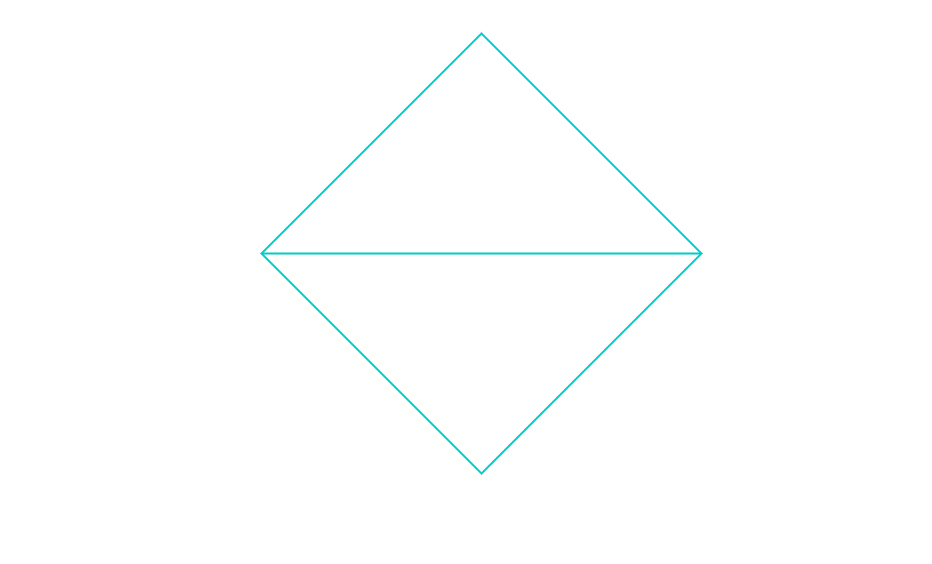
Using this model, analysts can start to piece together the different features of the cyber intrusion targeting Macron’s En Marche party, and begin to understand the potential adversary behind the attack. Whilst the French government has not publicly attributed the intrusion to any specific actor, and neither will this blog post, cybersecurity firm Trend Micro have attributed the intrusion to APT28, a threat actor associated to Russian intelligence agencies.
We can, nevertheless, use the two transversal “social-political” and “technological” axis to guide our intuition about the adversary’s identity.
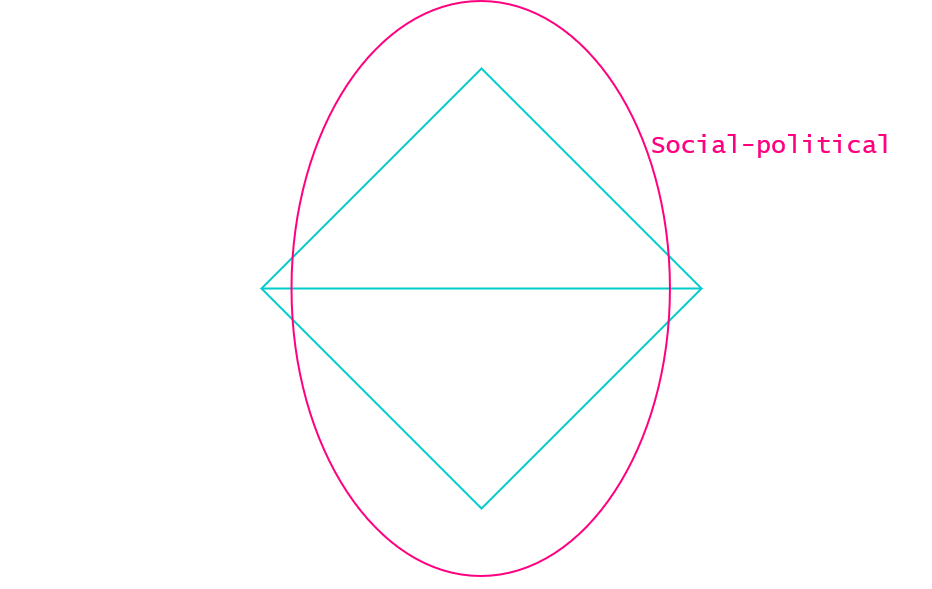
Using the lens of the social-political axis, we can consider the known observables for the Adversary and Victim features.
Victims include campaign staff supporting one of the 2017 French elections’ leading candidates, indicating that the adversary was likely attempting to influence the elections by collecting intelligence on the En Marche party. The adversary was able to enumerate that En Marche use OneDrive and register typosquatting domains, indicating a certain level of tradecraft and tailored targeting of the political party.
Known information also indicates that the adversary registered 3 of these domains using Ukrainian phone numbers, indicating a potential region of interest for investigators.
This leaves us with the following hypotheses:
- The adversary’s strategic goal was to interfere in the French presidential elections by compromising the campaign behind one of the leading candidates.
- The adversary tailored their targeting specifically to En Marche.
- Accounting for poor OPSEC (operational security), the adversary may be leveraging assets in Eastern Europe.
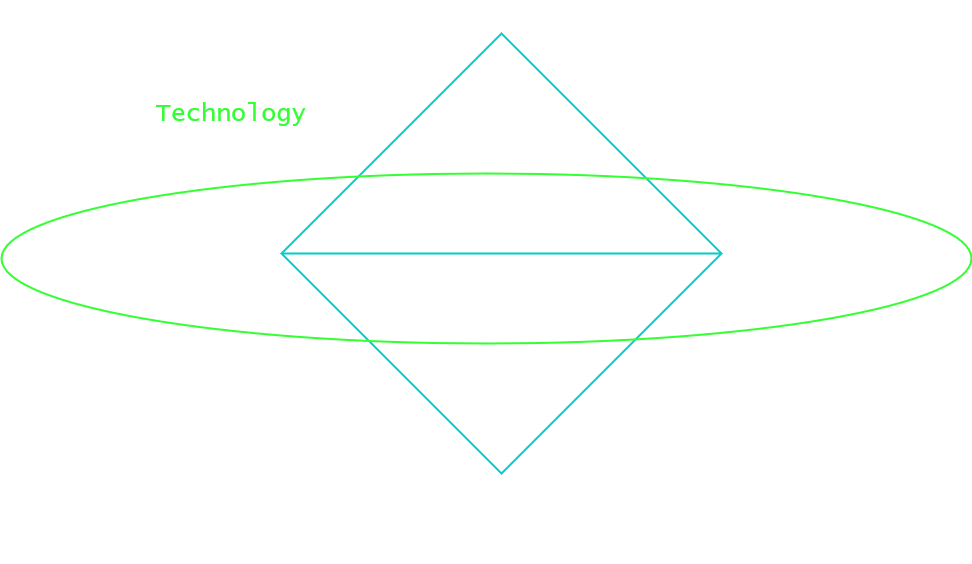
Using the lens of the technology axis, we can consider the known observables for the Infrastructure and Capability features in order to assess the nature of the adversary.
Capabilities that were observed being used during the En Marche intrusion do not demonstrate that the threat actor behind the intrusion was particularly sophisticated. Even in 2017, conducting phishing campaigns was within the realm of techniques, tactics and procedures (TTPs) regularly employed by cybercriminal and activist groups.
Despite this, two elements of the capabilities and infrastructure demonstrate that the campaign was nevertheless highly targeted in nature, which is less common amongst cybercriminal groups. The use of an email address typosquatting Mahjoubi’s name demonstrates that the actor had prior understanding of Mahjoubi’s role within the campaign and had specifically selected the campaign’s digital manager to dispel spear-phishing emails using cybersecurity as a lure. Furthermore, as mentioned above, the registered domain names indicate that the threat actor had conducted reconnaissance on En Marche’s technical infrastructure and was able to determine from either open or closed sources that En Marche used OneDrive for their document storage, once more revealing a highly targeted operation.
This results in the following hypotheses:
- The adversary’s capabilities include both political understanding and technical reconnaissance of En Marche, revealing a targeted and well-prepared reconnaissance phase prior to the intrusion.
- The advesary’s infrastructure further demonstrates that this strategic and tactical understanding of En Marche’s hierarchy and technical stack was translated into operational means being deployed in the form of domains typosquatting En Marche’s OneDrive.
As a result, we have the following synthesis of the nature of the adversary which conducted the intrusion:
- The adversary had a strategic interest in targeting En Marche at the height of the campaign for the 2017 French presidential elections, and its highly targeted operation demonstrates that preparations and reconnaissance had begun prior to the intrusion, ruling out more opportunistic actors like cybercriminals.
- The specificity of the targeting within En Marche by targeting the campaign’s digital manager and using cybersecurity as a phishing lure demonstrates experience in targeting similar organisations, meaning that the intrusion was likely the work of a persistent threat actor. This rules out lesser resources actors like activists.
- Three of the four typosquatting domains were registered using Ukrainian phone numbers, potentially revealing that the actor employs assets in Ukraine, potentially leading to regional actors.
Using known observables and the diamond model, analysts can reach a number of hypotheses which provide this analytical basis for further attribution. Readers can reach their own conclusions as to the adversary that may correspond to the above hypotheses.
The Disinformation campaign
Following the intrusion on 3 May, on 5 May 9 gigabytes of data were posted to Pastebin by a user named “EMLEAKS”. The leaked emails contained a majority of internal emails pertaining to the legitimate functioning of a political campaign at the height of the presidential elections. However, according to the Atlantic Council’s Digital Forensics Research Lab, several documents included in the leaks reportedly showed “evidence of offshore accounts, tax evasion, and a slew of other nefarious activities”. French media outlets and fact-checking organisations analysed the contents and subsequently assessed that the compromising documents were likely forgeries purposefully added to the corpus of legitimate emails (T0025).
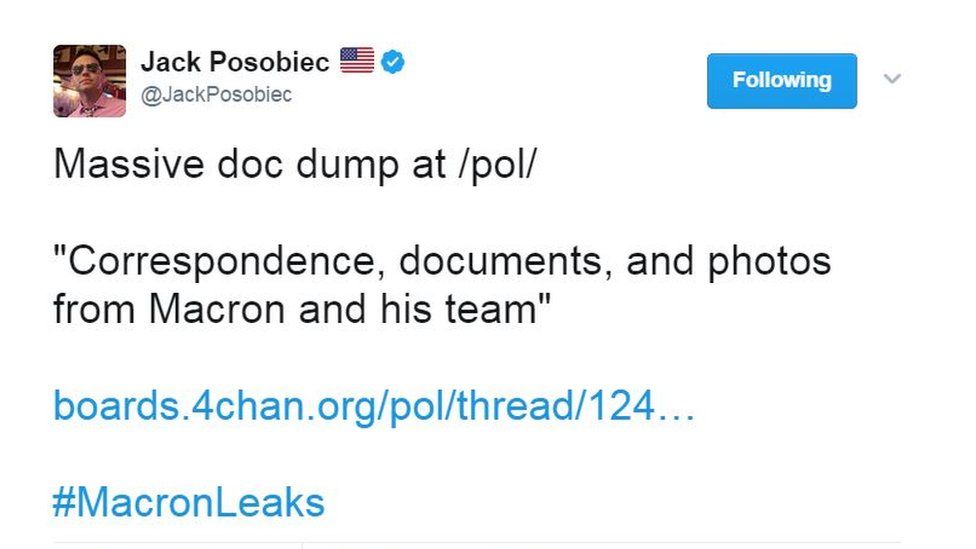
Nevertheless, the leak gained traction online following the posting of the leaks to 4chan’s /pol/ section, a notorious forum hosting alt-right content by anonymous posters. An anonymous user posted the Pastebin link. The user then posted several replies in the same thread, indicating that an analysis of the documents would be hosted on nouveaumartel[.]com.
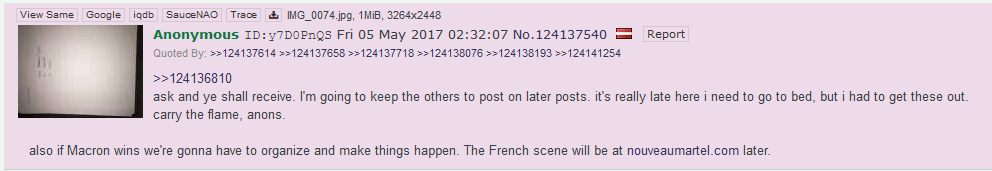
Figure 1: One of the posts by the anonymous user who originally uploaded the leaked En Marche documents to 4chan[1]
Analysis of the posts and WHOIS information for the domain revealed three crucial observables: first, the registered username for the domain was listed as “weev”, a notorious Neo-Nazi hacker known to be responsible for the web infrastructure for the Daily Stormer, a Neo-Nazi website. Second, the anonymous user who posted the links boasted a Latvian flag, indicating that they had posted from a Latvian IP address. Third, the domain was hosted on Latvian infrastructure, which overlapped with infrastructure used to host the Daily Stormer. These observables indicate that weev was highly likely the original poster of the leaks on 4chan, indicating the potential use of American alt-right and neo-nazi figures to disseminate the hacked emails.
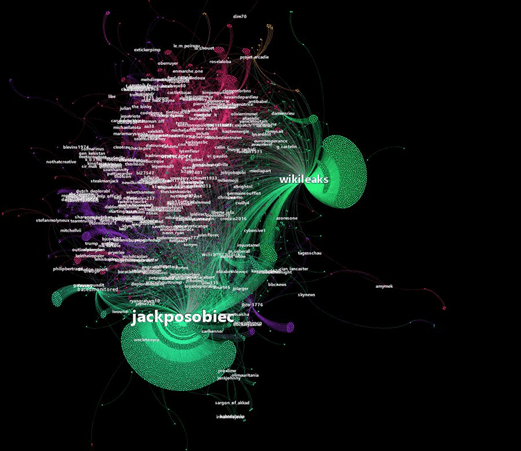
The leaks were initially propagated on mainstream social media platforms like Twitter by Jacob Posobiec, an American alt-right figure, followed by the official Wikileaks Twitter account. According to DFR Labs, the #MacronLeaks hashtag first used by Posobiec started gaining considerable traction on Twitter on the evening of 5 May, with “the ten most active accounts to use the #MacronLeaks hashtag posted over 1,300 tweets in just over three hours, another classic sign of bot use” (T0038, T0049, T0054). The leaks were also propagated by both English and French-speaking users on other platforms such as Discord and Reddit. Although pro-Russian accounts accounted for only roughly 1.5% of the activity around the #MacronLeaks conversation on Twitter, they were estimated to be twice as active as accounts associated to anti-Macron and alt-right accounts.
There was also evidence of automated activity (bots) around the #MacronLeaks hashtag, with many bot accounts “originally created shortly prior to the 2016 US presidential election and used to support the same views in the context of American politics”, with the accounts being re-activated in May 2017 to “push #MacronLeaks”.
The leaked documents were largely benign- however, several documents included in the leak provided a basis for messaging on social media platforms. One document purportedly provided evidence of Macron working with a Lebanese businessman to sell weapons to ISIS in France, whilst another alleged that En Marche staff had purchased cocaine for Macron. Lastly, another email alleged that Macron was on the mailing list of a gay underwear brand. These three documents were used to push messaging around three topics on social media platforms:
- Macron’s purported ties with ISIS as an addition to his perceived lack of an electoral programme to fight islamist extremism following the 2015 terror attacks
- Macron’s use of illegal drugs as indicative of Macron’s social deviance, in connection to narratives around his background in the banking sector prior to public office
- Macron’s alleged homosexuality as indicative of Macron’s overall social deviance, connected to messaging around his relationship with his wife, Brigitte Macron
Subsequent analysis of the documents by the Bulgarian investigative outfit Bivol revealed several further observables surrounding the falsification of documents included in the leak. The documents’ metadata indicated that the documents were last modified on May 3rd, the day the intrusion took place and two days prior to their publication online. Furthermore, according to Jeangène-Vilmer’s report, Bivol demonstrated that documents were scanned using “two professional Canon machines, costing $29,999 and over $100,000 respectively” – indicating that the falsification of documents was likely carried out by actors with access to significant resources, hence likely excluding “amateur forgery by Macron’s opponents and Le Pen’s fans.” Lastly, metadata analysis by Bivol revealed that the last person to have edited several documents was listed as “Рошка Георгий Петрович”, the name of an employee working at a Eureca, a Russian IT company whose clients include the Russian Ministry of Defence and the FSB intelligence agency.
Furthermore, the publication of this data on the evening of 5 May came hours before the start of the legally-mandated “media blackout” prior to the second round of the Presidential elections on 7 May, whereby a blanket ban on media, government and campaign electoral activity and communications came into rigor. The timing of the publication suggested that the adversary intentionally leveraged the media blackout to prevent any public response from En Marche or the French government pertaining to the intrusion and subsequent disinformation campaign. This indicates a prior understanding of the French electoral system and intent to translate this understanding into an operational decision to leak the exfiltrated emails and amplify them on social media at a time where victims could not issue denials or rebuttals of the amplified disinformation.
Applying the diamond model of disinformation
Returning to the diamond model of disinformation, we now have a list of observables we can populate in each of our four features. These observables are the following:
Adversary:
- Metadata analysis of the forged documents reveals that some of the documents were scanned using industrial-grade printing equipment, denotating a high level of resources.
- Metadata analysis also revealed that forged documents contained an author value set to the name of an employee of Eureca, a Russian IT company with connections to the Russian state.
- Given the timing of the leak and its amplification on social media, the overall intent of the disinformation campaign was to influence French voters ahead of the second round of the elections.
- Given the timing of the leak in relation to the electoral media blackout, this demonstrates that actor has an understanding of French electoral legislation and sought to use the blackout to their advantage as to prevent a coordinated response to the campaign.
Mediums:
- The leaks were originally posted on archive.org and shared using Pastebin.
- The leaks were then disseminated on 4chan and nouveaumartel.com before being shared on mainstream social media platforms such as Twitter, Discord and Reddit, demonstrating a cross-platform approach to the disinformation campaign.
- The leaks were amplified on Twitter by both English and French-speaking alt-right activists including Jacob Posobiec, who started the #MacronLeaks hashtag.
- The use of US alt-right activists and WikiLeaks to disseminate hacked materials is a tactic that has been leveraged in the amplification of previous hack-and-leak operations such as the DNC hack.
- Analysis of Twitter activity demonstrates that bots previously used for the 2016 US elections were re-activated to spread the #MacronLeaks hashtag.
Messages:
- Common messaging and narratives observed being amplified on social media based on the leaked emails include:
- Macron’s alleged offshore accounts demonstrating fiscal evasion. Fiscal evasion and mishandling of public finances is a major point of friction in French politics, as demonstrated by the Fillon scandal earlier in the same campaign.
- Macron’s purported ties to a Lebanese businessman responsible for providing weapons to French ISIS cells. This messaging sought to contribute to the overall narrative that Macron was involved in the sponsoring of ISIS at a time where Islamic extremism and public responses to terrorism were a major element of political friction following the 2015 terror attacks.
- The role of En Marche staff in purchasing cocaine for the candidate. messaging supported the wider narrative of corruptness of the party, candidate, and French politics as a whole.
- Macron’s alleged closeted homosexuality as demonstrated by his subscription to a mailing list for a gay underwear brand. This messaging joined earlier allegations that the candidate was having an affair with the head of a major radio station in an overall narrative attempting to prove Macron’s social deviance.
Victims:
- The victims of the disinformation campaign does not only include Macron and En Marche specifically but also the wider French public, as the leak was scheduled 48 hours before the decisive second round of the presidential elections.
- The adversaries sought to exploit several societal vulnerabilities and domestic political friction, including:
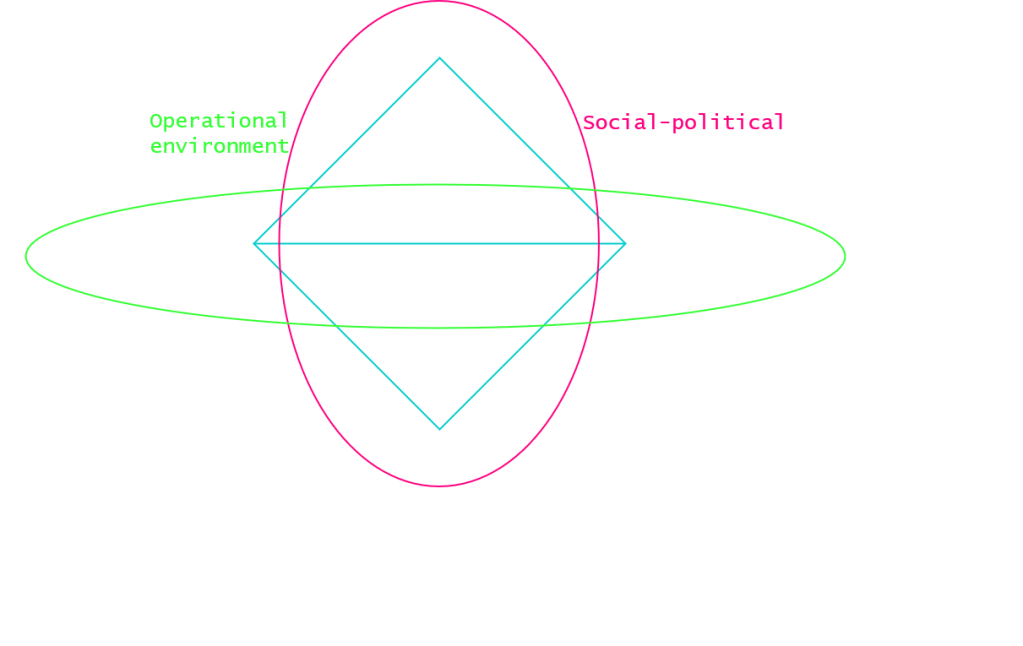
We can also leverage the “operational environment” and “social-political” axis of the diamond model for analysis.
Firstly, the operational environment demonstrates that the adversary has employed a significant range of capabilities over the course of the #MacronLeaks disinformation campaign, demonstrating a mature playbook in influencing elections. Evidence suggests that the #MacronLeaks contained both messaging and mediums that were previously employed during the 2016 US elections.
- The use of forgeries and hacked materials was a tactic that was previously employed during the 2016 US elections with the DNC hack.
- The use of influencers and outlets like the US alt-right and WikiLeaks to disseminate hacked materials and amplify disinformation was also a feature of the 2016 elections.
- Finally, the use of automated accounts (bots) that were observed supporting Donald Trump during the 2016 US elections also demonstrates access to a high level of resources such as dormant political botnets.
- Fiscal evasion, funding ISIS, drug use and sexual deviance were all narratives used to discredit Hillary Clinton in the 2016 US elections.
Secondly, the social-poltiical axis suggests that the adversary had a significant understanding of the French political landscape and intent to influence French voters. This includes:
- Knowledge of French electoral law around media blackouts, timing the release of the leak several hours before the start of the media blackout
- Timing the leak before the decisive round of the elections in an attempt to sway voters, demonstrating intent to influence the outcome of the presidential elections
- Knowledge of existing political frictions such as corruption, tax evasion as well as sexual and social deviance by French political elites in addition to the societal trauma of the 2015 terror attacks.
The above analyses demonstrate that the adversary employed proven techniques over a period of time which includes significant preparation of both mediums and messaging as well as extensive research into the societal vulnerabilities that could be exploited during the 2017 French elections.
[1] https://archive.4plebs.org/pol/thread/124134731/#124137540
Leave a comment